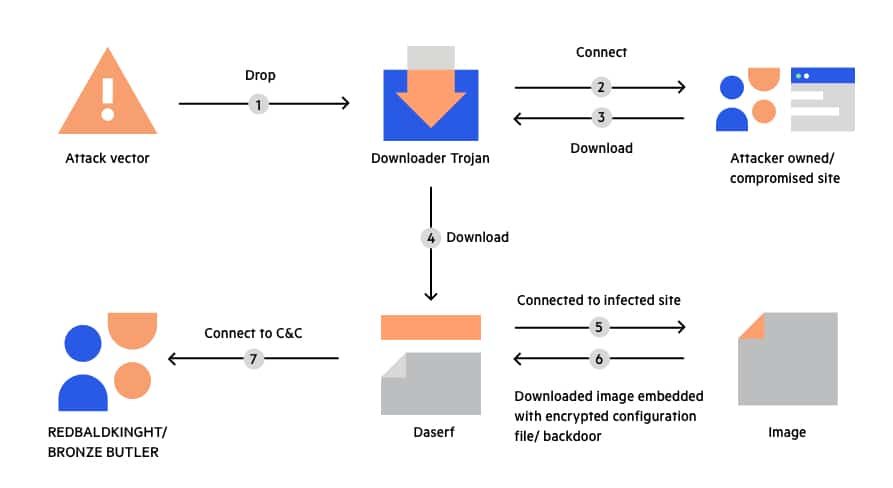
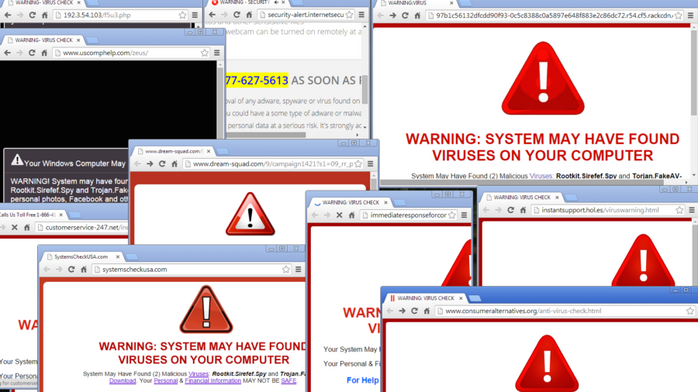
Trojan horse deals attack example
Trojan Horse Meaning Examples Prevention deals, Trojan Horse Virus Examples How to Defend Yourself deals, Trojan Horse Meaning Examples Prevention deals, What is a Trojan Horse Virus Types Prevention in 2024 deals, What is a Trojan Virus Trojan Horse Malware Imperva deals, What Is a Trojan Horse in Computer Terms InfoSec Insights deals, What is a Trojan Horse Virus Definition Examples Removal Options Video deals, The Infamous Trojan Horse Virus What it is What it does Web deals, Different Examples of a Trojan Horse Types of Trojan Horse deals, What is a Trojan Horse Virus Types Prevention in 2024 deals, What is a Trojan horse attack Shiksha Online deals, What is a Trojan Horse Virus Types and How to Remove it deals, What is Trojan Horse Malware and how can you avoid it deals, What Is a Trojan a Virus or Malware How Does It Work Avast deals, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus deals, What is a Trojan Horse Virus Attack Littlefish Guide deals, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses deals, No money but Pony From a mail to a trojan horse Malwarebytes Labs deals, Personal Protection Against the Trojan Horse All About Trojan deals, Placeholder Trojan Writing a Malware Software deals, What is a Trojan Horse U.S. News deals, What is Trojan Horse Computing zenarmor deals, What Is a Trojan Virus Definition Types Prevention Tips deals, Placeholder Trojan Writing a Malware Software deals, What Is a Trojan Horse in Computer Terms InfoSec Insights deals, Malware Based Phishing Attacks 101 What is Malware Phishing deals, Trojan Horse The Basics XtraWeb deals, What is a Trojan horse attack Shiksha Online deals, What Are Trojans How Can You Protect Yourself deals, AIDS Trojan horse Wikipedia deals, Remove deals, Viruses worms and Trojan horses in network security Difference between Virus worm and Trojan Horse deals, What Is a Trojan Horse in Computer Terms InfoSec Insights deals, How trojan malware is evolving to survive and evade cybersecurity deals, 7 Phases of a Trojan Horse Attack Edafio deals.
-
Next Day Delivery by DPD
Find out more
Order by 9pm (excludes Public holidays)
$11.99
-
Express Delivery - 48 Hours
Find out more
Order by 9pm (excludes Public holidays)
$9.99
-
Standard Delivery $6.99 Find out more
Delivered within 3 - 7 days (excludes Public holidays).
-
Store Delivery $6.99 Find out more
Delivered to your chosen store within 3-7 days
Spend over $400 (excluding delivery charge) to get a $20 voucher to spend in-store -
International Delivery Find out more
International Delivery is available for this product. The cost and delivery time depend on the country.
You can now return your online order in a few easy steps. Select your preferred tracked returns service. We have print at home, paperless and collection options available.
You have 28 days to return your order from the date it’s delivered. Exclusions apply.
View our full Returns and Exchanges information.